- Fraud HQ
- Posts
- FBI Warns of Fake IC3 Websites Used in New Spoofing Scams
FBI Warns of Fake IC3 Websites Used in New Spoofing Scams


A Detective’s Perspective on Fraud and Scams
“I will fight for those who cannot fight for themselves.” — Wonder Woman
This issue’s cases show just how relentless and creative fraudsters have become. From fake FBI websites to Bitcoin ATM scams targeting seniors, no one is off limits. Whether it’s a teen SIM-swapper stealing millions with just his voice, or global sextortion rings preying on the vulnerable, the message is clear: those with the power to protect must step up for those who need it most.
Hero Briefing
FBI Warns of Fake IC3 Websites Used in New Spoofing Scams
SIM Swapper Sentenced: The Teen Who Stole Millions Using His Voice
Elderly Woman Scammed Out of $25,000 via Bitcoin ATM
Nigerian Man Extradited in $2M Sextortion and Romance Scam
PayPal Scam Nearly Catches Woman During Lunch
FBI Warns of Fake IC3 Websites Used in New Spoofing Scams
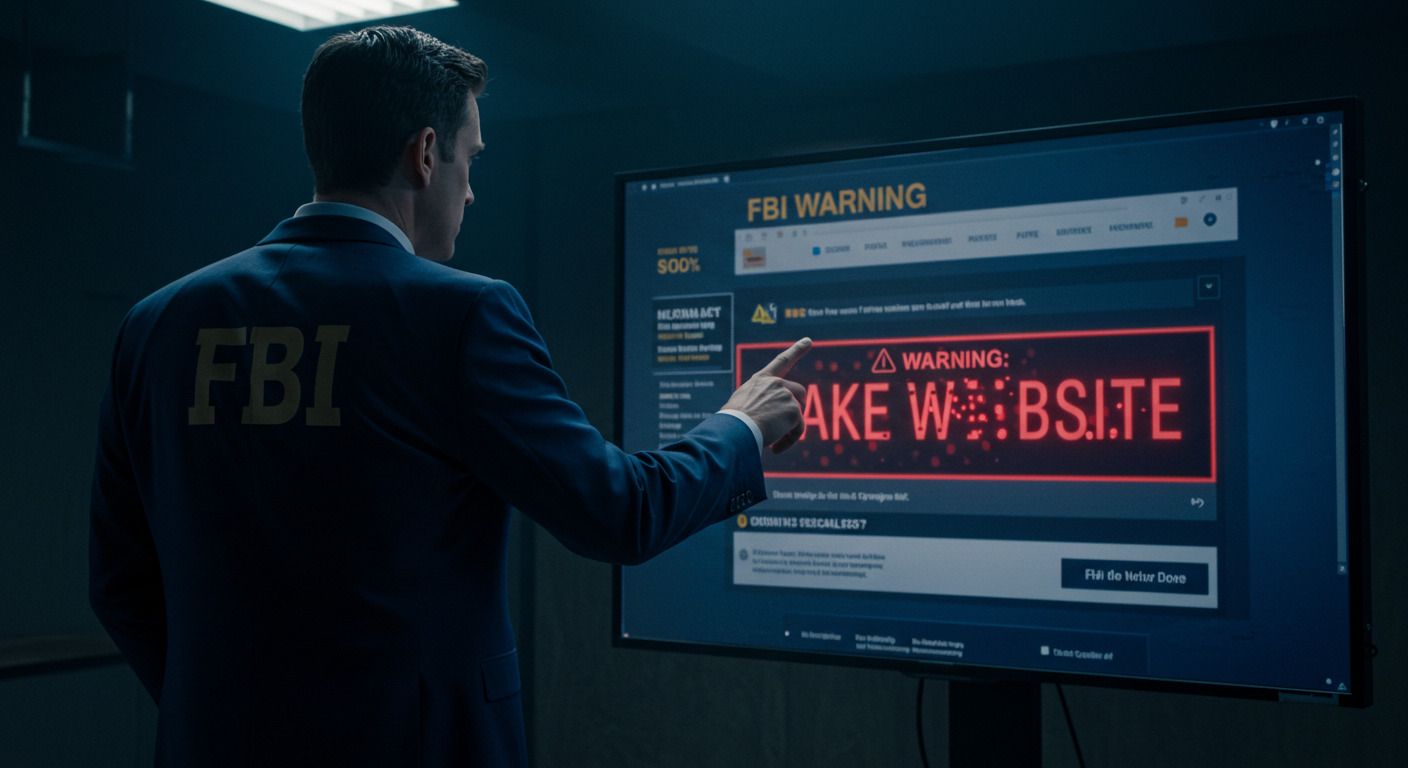
The Intel:
The FBI has issued a public alert warning that scammers are spoofing the official Internet Crime Complaint Center (IC3) website in an attempt to steal sensitive personal and financial information from victims.
Cybercriminals are creating fraudulent websites with slight misspellings or alternative domain endings to impersonate the real IC3 site. These fake pages are then used to gather private details like names, addresses, banking credentials, and more from people attempting to report fraud or recover stolen funds.
As someone who has worked with and used the IC3 website, it is one of the more important report taking systems to help identify and combat scams.
Why it matters:
Victims seeking help could land on a scam site and unknowingly give sensitive info to criminals.
Fake sites may look nearly identical but use .com, .org, or .net instead of .gov.
Some spoofed sites have asked for upfront “recovery” payments, which the real IC3 never does. These scams hurt trust in legitimate law enforcement channels and add to victim trauma.
Even more importantly, victims may be re-victimized by criminals posing as FBI agents and other law enforcement officials causing more harm and financial loss.
Detective’s Insights:
Even Fraud Reporting Is Being Exploited
These fake websites are often promoted through ads or manipulated search results
Scammers exploit urgency and victims desperate to recover money may not notice slight domain differences
The goal is clear: harvest your personal data or scam you further under the guise of official recovery help
IC3 will NEVER ASK YOU TO PAY to file a report or recover stolen funds
Takeaway:
Always type WWW.IC3.GOV directly into your browser. Never rely on search engines
Avoid sponsored ads when searching for government sites
Confirm the website ends in “.gov” and contains no spelling errors
Never share sensitive information unless you’re sure the site is legitimate
Remember: IC3 has no social media presence and will never refer you to recovery services requesting payment
SIM Swapper Sentenced: The Teen Who Stole Millions Using His Voice

The Intel:
Noah Michael Urban, a 20-year-old from an affluent California suburb, has been sentenced to 10 years in federal prison for his role in a nationwide SIM swapping ring that stole millions from cryptocurrency investors by tricking employees at the Big 3 in the telco world. AT&T, T-Mobile, and Verizon.
Urban wasn’t a coder or hacker. He was a smooth-talking social engineer who manipulated phone company workers into giving him access to internal systems.
Honestly, based on investigative experience, he probably wasn’t really that smooth. He later used that access to transfer victims’ phone numbers to SIM cards in his possession.
That’s all it took to intercept multi-factor authentication codes and drain crypto wallets.
Why it matters:
Social engineering, not hacking, was the real weapon. SIM swapping attacks are often launched without writing a single line of code.
Noah and his teenage crew stole millions in cryptocurrency just by talking their way in. He built a mini criminal enterprise even paying others up to $4,000 per successful social engineering call
Many SIM swappers are under 21, socially awkward, and drawn in through gaming platforms like Minecraft. For them, the scam was game.
Detective’s Insights:
This Wasn’t a Tech Breach. It Was a Human Breach.
Carriers like AT&T, T-Mobile, and Verizon were outmaneuvered by teenagers
He recruited others, outsourced the dirty work, and made himself a millionaire
SIM swappers often pose as tech support, internal employees, or security staff
The real issue? MFA tied to phone numbers is no longer safe
Takeaway:
Use app-based authentication (like Proton Authenticator or Google and Microsoft Authenticators) instead of SMS
✅ Lock your SIM to your mobile carrier account. Contact your carrier for this.
✅ Never share login or recovery info. Even if the caller sounds “official”
✅ Enable account alerts for any carrier or bank activity.
Elderly Woman Scammed Out of $25,000 via Bitcoin ATM

The Intel:
A 79-year-old Wilkes-Barre woman was manipulated into converting $25,000 in cash into Bitcoin after receiving a fraudulent alert claiming her bank account had been compromised.
She called the number displayed on the fake warning and was quickly coached by the scammer on how to withdraw her money and deposit it into a Bitcoin ATM controlled by the criminals.
Authorities say the suspect provided step-by-step instructions on how to complete the transaction, ensuring the stolen funds would be difficult to trace and recover once converted.
Why it matters:
Scammers exploit fear and urgency, especially with seniors who trust authority figures. Victims are tricked into using crypto ATMs, a favorite tool for fraudsters due to lack of oversight.
These scams combine tech support lies with bank impersonation tactics to convince people to act fast. The median age of victims in crypto ATM scams is often 65+—this is a senior citizen crisis
Detective’s Insights:
I see this scam happen every single day
The scam likely started with a fake pop-up mimicking antivirus or bank alerts
The scammer coached the victim live on the phone, exploiting her confusion and trust
Bitcoin ATMs are very difficult to trace, and many operators refuse to refund victims
Bitcoin ATM scams usually involve fake warrants, tech support imposters, government imposters, and romance scams.
Takeaway:
✅ Never call numbers that pop up on your screen. Real banks never do this
✅ Pause before withdrawing large sums of money, especially if urged to use crypto
✅ Bitcoin ATMs should never be used for payments or refunds
✅ If a call or message sounds urgent and emotional, hang up and call your bank directly
Nigerian Man Extradited in $2M Sextortion and Romance Scam Targeting U.S. Victims
The Intel:
Olamide Shanu of Lagos, Nigeria, has been extradited from the UK to the U.S. to face eight federal charges linked to a large-scale sextortion and romance scam operation.
Shanu and his co-conspirators allegedly posed as women online, convincing men to send explicit images, then extorting them by threatening exposure unless they paid up.
Victims included individuals across the U.S., including a college student in Idaho. The group also ran romance scams, laundered money via peer-to-peer apps and cryptocurrency, and transferred proceeds back to Nigeria.
Why it matters:
Global scam operations continue to target Americans, exploiting emotions, trust, and digital platforms.
Romance scams and sextortion are increasingly entangled with cryptocurrency laundering and cross-border fraud.
The case underscores the growing collaboration between international law enforcement agencies to bring cybercriminals to justice. It highlights the severe psychological and financial toll on victims, many of whom are young, isolated, or emotionally vulnerable.
Detective’s Insight:
This Wasn’t Random. It Was a Coordinated Attack
Victims were carefully groomed over time, then suddenly extorted
The same tactics used in romance scams, emotional bonding, false trust, urgency, were used here
Sextortion cases often go unreported due to shame, meaning the real victim count is likely much higher
Crypto wallets and P2P apps like Cash App, Apple Pay, and Zelle were likely used moving funds in and out of the U.S.
Takeaway:
✅ Never share explicit photos or videos online, even in private messages
✅ If someone pressures you for sexual content, stop engaging and report their account
✅ Don’t pay extortion demands. Once you pay, the blackmail usually continues
✅ Talk to teens and young adults about the risks of digital relationships and scams
✅ If you’re a victim, report immediately to IC3.gov and contact local law enforcement. YOU ARE NOT ALONE!
PayPal Scam Nearly Catches Woman During Lunch

The Intel:
While enjoying lunch with her 90-year-old grandmother, Stephanie Moore received what looked like a legitimate PayPal receipt on her phone. Without hesitation, she opened it but it was a scam.
Thankfully, Stephanie avoided losing money only because her PayPal account had no funds. But her experience is a powerful reminder: these scams are timed to catch you when you’re busy or distracted.
Why it matters:
83% of payment app users (PayPal, Zelle, Venmo) reported being targeted by scammers in 2024. More than half of those targeted lost money.
PayPal was the third most impersonated company in 2023 (FTC: ~10,000 scam reports). AI-powered emails now look more polished, professional, and convincing than ever.
Detective Insights:
These scams use urgency and timing to get people to act without thinking like during family time, commuting, or work
Criminals know most people skim emails, so logos and payment references are designed to mimic real notifications
The scam often includes a fake support number, luring victims into calling and giving up credentials or sending money
Even if your account is empty, linking a card or bank account can put you at risk if you fall for the trick
Takeaway:
✅ Pause and verify: Don’t open emails or click links while distracted
✅ Always log in directly to PayPal or any app. Never use emailed links
✅ Look out for typos, odd sender addresses, or urgency
✅ If you get a suspicious message, contact the company directly through their website or app
✅ Consider unlinking cards from payment apps unless actively using them
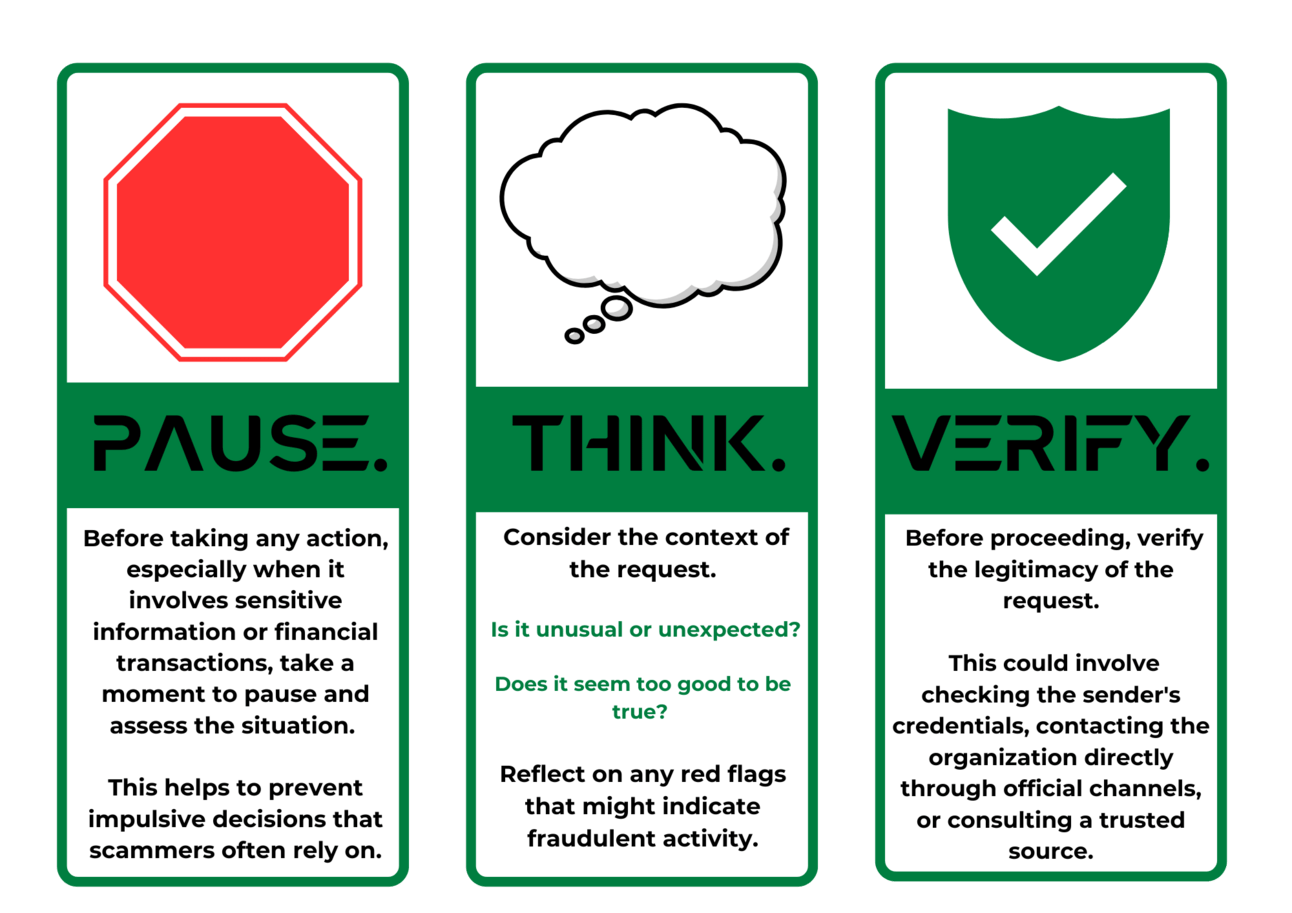
At the end of the day, the most powerful defense against social engineering isn’t technology. It’s awareness. Scammers rely on speed and emotion to trap you, but the Pause, Think, Verify method breaks that cycle. Pause before reacting to pressure. Think about whether the message or request makes sense. Verify through trusted, official channels before taking action.
Whether it’s an everyday consumer or a celebrity being impersonated, the playbook for prevention is the same: slow down, stay skeptical, and confirm before you comply. Stopping scams starts with taking back control of the moment.